What are the HIPAA Breach Notification Requirements?
The HIPAA breach notification requirements are that HHS’ Office for Civil Rights and individuals whose unsecured Protected Health Information (PHI) has been exposed must be notified within a specified timeframe. Different timeframes exist for notifying a breach to HHS’ Office of Civil Rights depending on the number of records breached, and it is important that covered entities develop a breach response plan to ensure breaches of unsecured PHI are made in a timely manner.
While most HIPAA covered entities should understand the HIPAA breach notification requirements, organizations that have yet to experience a data breach may not have a good working knowledge of the requirements of the Breach Notification Rule. Business associates that have only just started providing a service to Covered Entities may similarly be unsure of the reporting requirements and actions that must be taken following a breach.
The issuing of notifications following a breach of unencrypted PHI is an important element of HIPAA compliance. The failure to comply with HIPAA breach notification requirements can result in a significant financial penalty in additional to that impose for the data breach itself. With this in mind, we have compiled a summary of the HIPAA breach notification requirements for covered entities and business associates.
Summary of the HIPAA Breach Notification Rule
The HIPAA Breach Notification Rule – 45 CFR §§ 164.400-414 – requires covered entities to report breaches of unsecured electronic protected health information and physical copies of protected health information. A breach is defined as the acquisition, access, use, or disclosure of unsecured protected health information in a manner not permitted by HIPAA Rules.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please Enter Correct Email Address
Your Privacy Respected
HIPAA Journal Privacy Policy
According to the HHS´ guidance on the HIPAA Breach Notification Rule, an impermissible use or disclosure of unsecured protected health information is presumed to be a breach unless the covered entity or business associate demonstrates there is a low probability the protected health information has been compromised based on a risk assessment of at least the following factors:
- The nature and extent of the protected health information involved, including the types of identifiers and the likelihood of re-identification;
- The unauthorized person who used the protected health information or to whom the disclosure was made;
- Whether the protected health information was actually acquired or viewed; and
- The extent to which the risk to the protected health information has been mitigated.
HIPAA breaches include unauthorized access by employees as well as third parties, improper disclosures, the exposure of protected health information, and ransomware attacks. Exceptions include: Breaches of secured protected health information such as encrypted data when the key to unlock the encryption has not been obtained; “any unintentional acquisition, access, or use of protected health information by a workforce member or person acting under the authority of a covered entity or a business associate, if such acquisition, access, or use was made in good faith and within the scope of authority and does not result in further use or disclosure;” An inadvertent disclosure by a person who is authorized to access PHI, to another member of the workforce at the organization who is also authorized to access PHI; When the covered entity or business associate makes a disclosure and has a good faith belief that the information could not have been retained by the person to whom it was disclosed.
In the event of a reportable HIPAA breach being experienced, the HIPAA breach notification requirements are:
1. Notify Individuals Impacted – or Potentially Impacted – by the Breach
All individuals impacted by a data breach, who have had unsecured protected health information accessed, acquired, used, or disclosed, must be notified of the breach. Breach notifications are also required for any individual who is reasonably believed to have been affected by the breach.
Breach notification letters must be sent within 60 days of the discovery of a breach unless a shorter breach notification timeframe exists under state law or a request to delay notifications has been made by law enforcement. While it is permissible to delay reporting of a breach to the HHS for breaches impacting fewer than 500 individuals (see below), that delay does not apply to notifications to breach victims. Breach notification letters should be sent by first class mail to the last known address of breach victims, or by email if individuals have given authorization to be contacted electronically.
The HIPAA breach notification requirements for letters include writing in plain language, explaining what has happened, what information has been exposed/stolen, providing a brief explanation of what the covered entity is doing/has done in response to the breach to mitigate harm, providing a summary of the actions that will be taken to prevent future breaches, and giving instructions on how breach victims can limit harm. Breach victims should also be provided with a toll-free number to contact the breached entity for further information, together with a postal address and an email address.
2. Notify the Department of Health and Human Services
Notifications must be issued to the Secretary of the Department of Health and Human Services, via the Office for Civil Rights breach reporting tool. The HIPAA breach notification requirements differ depending on how many individuals have been impacted by the breach.
When the breach has impacted more than 500 individuals, the maximum permitted time for issuing the notification to the HHS is 60 days from the discovery of the breach, although breach notices should be issued without unnecessary delay. In the case of breaches impacting fewer than 500 individuals, HIPAA breach notification requirements are for notifications to be issued to the HHS within 60 days of the end of the calendar year in which the breach was discovered.
3. Notify the Media
HIPAA breach notification requirements include issuing a notice to the media. Many covered entities that have experienced a breach of protected health information notify the HHS, relevant state attorneys general, and the patients and health plan members impacted by the breach, but fail to issue a media notice – a violation of the HIPAA Breach Notification Rule.
A breach of unsecured protected health information impacting more than 500 individuals must be reported to prominent media outlets in the states and jurisdictions where the breach victims reside – See 45 CFR §§ 164.406. This is an important requirement, as up-to-date contact information may not be held on all breach victims. By notifying the media, it will help to ensure the maximum number of breach victims possible are made aware of the potential exposure of their sensitive information. As with the notifications to the HHS and breach victims, the media notification must be issued within 60 days of the discovery of the breach.
4. Post a Substitute Breach Notice on the Home Page of the Breached Entity’s Website
In the event that up-to-date contact information is not held on 10 or more individuals that have been impacted by the breach, the covered entity is required to upload a substitute breach notice to their website and link to the notice from the home page. The link to the breach notice should be displayed prominently and should remain on the website for a period of 90 consecutive days. In cases where fewer than 10 individuals’ contact information is not up-to-date, alternative means can be used for the substitute notice, such as a written notice or notification by telephone.
Data Breaches Experienced by HIPAA Business Associates
One often overlooked area of the HIPAA Security Rule in that Business Associate Agreements must stipulate that all security incidents must be reported by a business associate to a covered entity whether they result in a data breach or not (see 45 CFR §164.314(a)(2)(i)).
If a security incident does result in a breach of unsecured PHI, it must be reported to the covered entity within 60 days of the discovery of a breach. While this is the absolute deadline, business associates must not delay notification unnecessarily. Unnecessarily delaying notifications is a violation of the HIPAA Breach Notification Rule.
It is usually the covered entity´s responsibility to issue breach notifications to affected individuals, so any security incidents reported to the covered entity need to include details of the individuals impacted. It is a good practice to alert covered entities to security incidents rapidly to prevent avoidable delays in notifying individuals.
There may be exceptions to the above processes if, for example, a business associate experiences a data breach while providing a service to multiple covered entities and if each Business Associate Agreement stipulates it is the business associate´s responsibility to issue breach notifications to individuals and HHS´ Office for Civil Rights. Nonetheless, in these circumstances it would still be necessary to advise each covered entity of the security incident that resulted in the data breach.
Timeline for Issuing Breach Notifications
Breach notifications should be issued as soon as possible and no later than 60 days after the discovery of the breach, except when a delay is requested by law enforcement. Investigating a breach of protected health information can take some time, but once all the necessary information has been obtained to allow breach notifications to be sent, they should be mailed.
HIPAA-covered entities must not delay sending breach notification letters. It is possible to receive a HIPAA violation penalty for delaying notifications, even if they are sent within 60 days of the discovery of the breach. There have been several recent cases of HIPAA breach notification requirements not being followed within the appropriate time frame, which can potentially result in financial penalties.
State Breach Notification Laws May Be Stricter than HIPAA
Most U.S. states have breach notification laws. Typically, notifications must be issued to breach victims promptly and a notice also submitted to the state attorney general’s office; and although many state breach notification laws exempt covered entities, they may not exempt business associates from providing breach notifications. In such cases, some states require breach notifications to be issued well within the HIPAA deadline.
Delaying breach notifications until the 60-day limit of HIPAA could well see state laws violated, leading to financial penalties from state attorney generals. State laws frequently change so it is important to keep up to date on breach notification laws in the states in which you operate.
Penalties for Violations of HIPAA Breach Notification Requirements
HIPAA covered entities must ensure the HIPAA breach notification requirements are followed or they risk incurring financial penalties from state attorneys general and the HHS’ Office for Civil Rights.
In 2017, Presense Health became the first HIPAA-covered entity to settle a case with the Office for Civil Rights solely for a HIPAA Breach Notification Rule violation – after it exceeded the 60-day maximum time frame for issuing breach notifications. Presense Health took three months from the discovery of the breach to issue notifications – A delay that cost the health system $475,000. The maximum penalty for a HIPAA Breach Notification Rule violation is $1,500,000, or more if the delay is for more than 12 months.
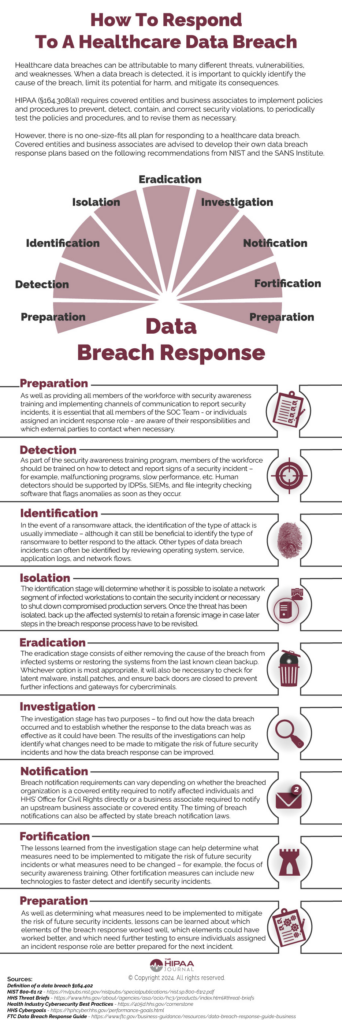
Responding to a Healthcare Data Breach
HIPAA Breach Notification Requirements FAQs
What is the difference between a HIPAA breach and a HIPAA violation?
The difference between a HIPAA breach and a HIPAA violation is that a HIPAA breach is when unsecured PHI is acquired, accessed, used, or disclosed in a manner not permitted by the Privacy Rule. A HIPAA violation occurs when a Covered Entity, Business Associate, or a member of the workforce fails to comply with any standard in the Privacy, Security, or Breach Notification Rules. It is not necessary for a breach to occur in order for there to be a HIPAA violation – for example, the failure to respond to a patient access request within 30 days is a HIPAA violation, but not a HIPAA breach.
Why must staff be trained on reporting HIPAA breaches?
Staff must be trained on reporting HIPAA breaches and other violations to their supervisors, managers, or the Privacy Officer. It is not necessary for staff to know the mechanics of the HIPAA breach notification requirements beyond that point, but they must be aware of the consequences of delaying a report in terms of the impact it will have on patients affected by the breach, the consequences for their employer if notifications are delayed longer than necessary, and on their own jobs if a breach comes to light weeks after it has happened.
What is the difference between secured PHI and unsecured PHI?
The difference between secured PHI and unsecured PHI is that secured PHI is defined as Protected Health Information that has been rendered unusable, unreadable, or indecipherable to unauthorized individuals through the use of technologies or methodologies specified in §13402 of the HITECH Act. HIPAA is technology neutral, but the implementation specifications relating to Access Controls and Transmission Security state encryption is required unless an equivalent protection is implemented, or the use of encryption is unreasonable and inappropriate in the circumstances.
What is an example of a “good faith belief” that PHI has not been retained?
An example of a good faith belief that PHI has not been retained is if, for example, a healthcare professional shows an X-ray image to a person not authorized to view the image. If the healthcare professional realizes the mistake and withdraws the X-ray image before it is likely any information relating to the image has been absorbed, it is highly likely that PHI has not been retained.
In this example, a Covered Entity can reasonably accept – in good faith – there has been no disclosure of unsecured PHI. However, it is important the healthcare professional still reports the unauthorized disclosure to a higher authority, and that the report – along with the good faith determination – is documented.
Why do individuals have to give authorization before they receive email notifications?
Individuals have to give authorization before they receive email notifications because email is not a secure communication channel. Covered Entities must obtain the authorization of an individual before sending an email that contains PHI; and, because breach notifications inform individuals what PHI was accessed, Covered Entities can only communicate a breach by email if they have a prior authorization.
When must a HIPAA breach be reported?
A HIPAA breach must be reported whenever unsecured PHI or ePHI has been used or disclosed impermissibly unless there is a low probability that data has been comprised based on the risk assessment mentioned above. Also mentioned above was the timetable for reporting HIPAA breaches – within sixty days if the breach involves 500 or more records, and by the end of the calendar year if the breach involves fewer than 500 records.
What is the HIPAA Breach Notification Rule?
The HIPAA Breach Notification Rule is a regulation introduced via the HITECH Act in 2009 that requires covered entities to notify affected individuals, HHS´ Office for Civil Rights, and – in some cases – the media when a breach of unsecured PHI occurs. Business associates are also covered by the Rule, and have to notify the covered entity of any security incidents.
Who does the Breach Notification Rule apply to?
The Breach Notification Rule introduced in the HITECH Act applies to HIPAA covered entities and business associates, and vendors of Personal Health Records (PNRs) and third party service suppliers with access to PNR identifiable health information. There is a difference in the breach notification rule requirements depending on the type of business:
- HIPAA covered entities are required to notify affected individuals, HHS´ Office for Civil Rights, and – where applicable – the media.
- Business associates are required to notify covered entities only unless a clause to the contrary appears in the Business Associate Agreement.
- Vendors of PNRs and third party service providers are required to report breaches of unsecured PNR information to affected individuals and the Federal Trade Commission.
What are the Breach Notification Rule requirements for business associates?
The Breach Notification Rule requirements for business associates are that, other than when stipulated in a Business Associate Agreement, business associates must report breaches of unsecured PHI to the covered entity with whom they have signed an agreement. Once the breach is reported to the covered entity, it is the covered entity´s responsibility to determine whether the breach is notifiable and, if so, to fulfil the HIPAA breach notification requirements.
When did the HIPAA breach notice requirements come into force?
The HIPAA breach notice requirements came into force on September 23, 2009. It should have been a week earlier, but the Department for Health and Human Services missed the deadline for publishing the Interim Breach Notification Final Rule in the Federal Register (it should have been within 180 days of the passage of HITECH) and still had to allow 30 days before the Rule took effect.
What are the necessary steps to notify a patient of a HIPAA violation?
The necessary steps to notify a patient of a HIPAA violation only apply if a HIPAA violation results in a breach of unsecured PHI. In such circumstances, each patient affected by the breach must be informed within sixty days of what happened, what information was disclosed, what the covered entity is doing to mitigate the consequences, and what actions the individual can take to reduce the potential for harm.
When must you report a healthcare disclosure incident?
You must report a healthcare disclosure incident on every occasion unless the disclosure qualifies as an incidental disclosure under §164.502 of the Privacy Rule. Even when you believe the disclosure may be incidental, it is still best to check whether the incident needs reporting with a person in authority (i.e., a HIPAA Privacy Officer) and document the report in case a complaint is later made by the individual whose healthcare information was disclosed.
Are there HIPAA violation reporting requirements?
In most cases there are HIPAA violation reporting requirements; but, unlike the HIPAA breach reporting requirements, each covered entity or business associate can determine what violations should be reported and who they should be reported to. Naturally, if a HIPAA violation results in a data breach, it is necessary for a covered entity to notify the affected individual(s) and HHS´ Office for Civil Rights, and for a business associate to notify the covered entity.
When must an individual be notified of a breach of their PHI?
An individual must be notified of a breach of their PHI anytime their individually identifiable health information is disclosed impermissibly. This not only means when a database is hacked or when an organization experiences a ransomware attack, but also if the individual´s PHI is disclosed verbally or used for a purpose not permitted by the Privacy Rule without authorization from the individual.
What must a HIPAA breach notification consist of?
What a HIPAA breach notification consists of varies according to who is doing the notifying and who the notification is to. For example, a HIPAA breach notification from a business associate to a covered entity only needs to consist of the name(s) of the individual(s) whose PHI has been breached – although it may be necessary to later supply further information for the covered entity to comply with their breach notification requirements.
A HIPAA breach notification from a covered entity to an individual has to notify the individual what happened, when it happened, how it happened, and what the covered entity is doing to mitigate the consequences. The notification has to advise the individual the types of PHI that were disclosed impermissibly, and explain how – depending on the types – they can protect themselves from fraud, loss, or theft. The notification should also include a toll-free number for further information.
When notifying HHS´ Office for Civil Rights of a data breach, the information required is event-specific inasmuch as the agency´s reporting portal consists of various paths depending on the nature of the breach, how it occurred, and what measures were in place to prevent the breach at the time – or have been implemented since. This PDFpublished by HHS´ Office for Civil Rights provides examples of the types of questions asked on the Breach Notification portal.
What happens after you have made a HIPAA data breach notification to HHS?
After you have made a HIPAA data breach notification to HHS, the notification is reviewed and the individual who reported the breach is contacted if further information is required – such as proof that HIPAA training was provided or that security solutions were implemented prior to the breach. If there is evidence to suggest the data breach is attributable to a HIPAA violation, HHS´ Office for Civil Rights may choose to conduct a compliance investigation on the covered entity.
If the investigation confirms the covered entity is not complying with the Privacy, Security, and/or Breach Notification Rules, the agency has the authority to offer technical assistance, impose a corrective action plan, or issue a civil monetary penalty. Alternatively, if PHI has been disclosed “knowingly and wrongfully”, the case could be referred to the Department of Justice, who will review the evidence before determining whether to pursue a criminal conviction.
In the event that ePHI is compromised, what are we required to do to comply with HIPAA law?
In the event that ePHI is compromised, what you are required to do to comply with HIPAA law depends on whether or not ePHI was secured, whether the incident resulted in an impermissible disclosure of ePHI, and whether you are a covered entity or business associate.
In the event that ePHI was secured with encryption so it is unusable, unreadable, or indecipherable to an unauthorized person, it is not necessary to do anything to comply with HIPAA law – unless the incident involves a ransomware attack, in which case compliance with the HIPAA breach reporting requirements are a “fact-specific determination” (see Item 6 on the HHS Ransomware Fact Sheet).
It may also not be necessary to do anything to comply with HIPAA law if ePHI was compromised but the event in which it was compromised did not result in an impermissible disclosure. For example, if a patient’s medical record was changed without authorization, but the issue was identified by an audit control and reversed, the event is not notifiable under the Breach Notification Rule.
If the compromise of ePHI has resulted in an impermissible disclosure and you are a business associate of a covered entity, you are required to report the incident to the covered entity at the earliest possible opportunity. The covered entity then takes over the responsibility for complying with HIPAA law unless there are clauses to the contrary in the Business Associate Agreement.
As a covered entity, you are required to notify a breach of unsecured ePHI to the affected individual(s) and HHS´ Office for Civil Rights. The processes for doing so appear in sections 45 CFR §164.400 to 45 CFR §164.414 of the Administrative Simplification Regulations and you have 60 days to complete the processes unless a state law stipulates a shorter time frame.
What is the difference between a HIPAA security breach and a HIPAA security incident?
The difference between a HIPAA security breach and a HIPAA security incident is that a breach of unsecured PHI is a reportable event whereas an incident does not necessary imply a breach has occurred – the Security Rule defining a security incident as “the attempted or successful unauthorized access, use, disclosure, modification, or destruction of information or interference with system operations in an information system.”
Therefore, an unauthorized attempt to access an information is not a HIPAA security breach if it is not successful. Similarly, a successful attempt to hack an information system is not a HIPAA security breach if PHI is not accessed, used, disclosed, modified, or destroyed. However, if these incidents occur on a business associate´s information system, they should be reported to the covered entity under the terms of a HIPAA-compliant Business Associate Agreement.
Who do you report a HIPAA violation to?
Who you report a HIPAA violation to – as opposed to a HIPAA breach – depends on your employer´s HIPAA policies. In most organizations, HIPAA violations should be reported to a manager or to the organization’s Privacy Officer; however, the correct procedures should have been explained to you during your initial HIPAA training.
What is a HIPAA violation?
A HIPAA violation is any failure to comply with the standards and implementation specifications in 45 CFR Parts 160, 162, and 164 by an organization that qualifies as a covered entity (generally health plans, health care clearinghouses, and healthcare providers) or that is a “business associate” of a covered entity with who PHI is shared.
The “Parts” (often referred to as the “Administrative Simplification Regulations”) include the General HIPAA Provisions, the Transactions and Code Set Rules, the Privacy Rule, the Security Rule, and the Breach Notification Rule. The standards in the Parts equally apply to members of a covered entity´s or business associate´s workforce and are enforced by workplace HIPAA policies.
What is an appropriate HIPAA breach response?
An appropriate HIPAA breach response depends on the nature of the breach and its cause. For example, the infographic above provides a 9-point HIPAA breach response which is appropriate for ongoing cyberattacks and can be adopted for other types of security incident. However, if a breach of unsecured PHI is attributable to a member of the workforce posting an image of a patient on social media, an appropriate breach response would be to follow the HIPAA breach notification requirements and sanction the member of the workforce for an impermissible disclosure of PHI.
Who are the federal and state regulators of the HIPAA Rules?
The federal and state regulators of the HIPAA Rules are the Department of Health and Human Services (HHS), the Federal Trade Commission (FTC), and State Attorneys General. Reports of HIPAA violations are investigated by HHS’ Office for Civil Rights. The agency has the authority to impose civil penalties or refer violations to the Department of Justice if criminal activity is suspected. Non-HIPAA covered organizations – such as vendors of health apps – are regulated by the FTC.
At a state level, HIPAA compliance is regulated by State Attorneys General. State Attorneys General can also initiate complaints from state residents relating to any failure to protect individually identifiable health information from impermissible uses and disclosures. Additionally, many states have privacy laws that pre-empt areas of HIPAA. Consequently, businesses need to be aware of which state laws apply to their activities in addition to HIPAA.
What sort of businesses would be regulated by the FTC rather than HHS?
The sort of business that would be regulated by the FTC rather than HHS is any business that is not a HIPAA covered entity or HIPAA business associate, but that creates, receives, maintains, or transmits individually identifiable health information. Since the passage of the HITECH Act in 2009, these businesses have had to comply with the Breach Notification Rule
Typically, these businesses include the manufacturers of health apps (i.e., fitness trackers) and connected devices (wearable blood pressure cuffs) if the products offer or maintain a personal health record (PHR) collected on consumers´ behalf. Additionally, vendors of software that accesses information in a PHR or sends information to a PHR are also subject to the Breach Notification Rule.
The Security Rule has “required” and “addressable” implementation specifications. What does this mean?
The Security Rule has “required” and “addressable” implementation specifications because some implementation specifications may not be reasonable or appropriate in all circumstances. In such circumstances, an addressable implementation specification allows Covered Entities to implement an alternative measure, provided the alternative measure is at least as effective and the reason for implementing it is documented.
Why doesn´t HHS recognize HIPAA certifications?
HHS doesn’t recognize HIPAA certifications because a HIPAA certification is a “point in time” accreditation that certifies a business complies with the HIPAA requirements at the time the certificate was issued. Under §164.308, businesses are required to conduct “periodic technical and non-technical evaluations”. Consequently, a point in time accreditation does not fulfil this requirement and – as HHS notes – does not “preclude HHS from subsequently finding a security violation”.
Where can I find the full text of the Administrative Simplification Regulations?
You can find the full text of the Administrative Simplification Regulations via a PDF compiled by the Department of Health and Human Services which can be downloaded from this page on the HHS website. For businesses unfamiliar with HIPAA, please note the PDF not only includes the Privacy, Security, and Breach Notification Rules (and the changes made to them by the HITECH Act), but also Transaction, Code Set, and Identifier Standards.
What are the Administrative Simplification Regulations?
The Administrative Simplification Regulations are Parts 160, 162, and 164 of the Code of Federal Regulations relating to Public Welfare. When HIPAA was passed in 1996, Congress instructed the Secretary of Health and Human Services to develop these Parts to cover compliance investigations and civil penalties (Part 160) and the transaction code sets (Part 162).
Part 164 of the Administrative Simplification Regulations contains the Rules most Covered Entities are familiar with – the Privacy, Security, and Breach Notification Rule – although rather than being included in HIPAA at the time the first two Rules were developed, the Breach Notification Rule was added following the passage of the HITECH Act in 2009.
Why do some businesses operating in the healthcare industry not have to comply with HIPAA?
Some businesses operating in the healthcare industry do not have to comply with HIPAA because they do not qualify as HIPAA Covered Entities. This may be because they do not conduct transactions for which HHS has published standards (i.e., a counsellor that bills clients directly), or because they do not conduct the transactions electronically (i.e., claims are sent via the mail).
However, if these businesses work for a Covered Entity as a Business Associate, they are required to comply with HIPAA to the extent agreed in the Business Associate Agreement. Furthermore, even if a healthcare provider does not have to comply with HIPAA because they do not qualify as a Covered Entity, they may still have to comply with other state and federal privacy regulations.
How might some businesses already have measures in place to comply with the Privacy Rule?
Some businesses might already have measures in place to comply with the Privacy Rule if, for example, they have areas of the waiting room sectioned off so healthcare professionals can discuss diagnosis with patients and their families in private, if they already have a “minimum necessary” policy, or if they allow patients to request a copy of their medical records.
How might some businesses already have measures in place to comply with the Security Rule?
Some businesses might already have measures in place to comply with the Security Rule if, for example, they enforce a password policy that requires users to create unique and complex passwords, if they run a security and awareness training program (which includes all members of the workforce), and if they maintain on-premises servers in a secure, access-controlled environment.
Why will most businesses have processes in place to comply with the Breach Notification Rule?
Most businesses will have processes in place to comply with the Breach Notification Rule because all 50 states, the District of Columbia, Guam, Puerto Rico, and the Virgin Islands have laws requiring private businesses, and – in most states – governmental entities to notify individuals of security breaches of information involving personally identifiable information.
Security breach laws typically have provisions regarding who must comply with the law (i.e., businesses, data or information brokers, healthcare providers, etc.), definitions of “personal information” (i.e., name combined with SSN, driver’s license or state ID, account numbers, etc.), what constitutes a breach (i.e., unauthorized acquisition of data), requirements for notice (i.e., timing or method of notice, who must be notified), and exemptions (i.e., for encrypted data).
How many states have medical privacy laws that can preempt HIPAA?
Forty-four states have medical privacy laws that can preempt HIPAA, but generally there may only be one or two clauses in the state regulations HIPAA Covered Entities have to be aware of. For example, in many states, a patient authorization is required before the patient’s HIV/AIDS status can be revealed by a healthcare provider (not required by HIPAA), or it may be the case that reports of child and elder abuse are mandatory (compared to being permitted by HIPAA).
What is a material change to policies and procedures that requires refresher HIPAA training?
A material change to policies and procedures that requires refresher HIPAA training is any change to a policy or procedure that affects the roles of members of the workforce. For example, if you change the procedures for requesting an accounting of disclosures, members of the workforce who respond to patients’ requests for an accounting of disclosures will have to be trained in the new procedures.
Is HIPAA refresher training mandatory?
HIPAA refresher training is mandatory when there is a material change to policies and procedures, but it is a best practice for Covered Entities to provide refresher training at least annually to prevent poor compliance practices creeping in. In addition, it is important to be aware that the security and awareness program required by the Security Rule is a “program” and not a one-off session. This implies security and awareness training should be ongoing and include references to HIPAA policies.
What difference does “a good faith attempt” at HIPAA compliance make following a data breach?
The difference a good faith attempt at HIPAA compliance can make following a data breach is significant. In January 2021, President Trump signed an amendment to the HITECH Act which gives HHS’ Office for Civil Rights enforcement discretion when calculating a civil monetary penalty following a data breach. Although the amendment doesn’t provide immunity from HIPAA penalties, HHS’ Office for Civil Rights has the authority to refrain from enforcing a penalty if there has been a good faith attempt to comply with HIPAA in the twelve months previous to a data breach.
Why is it in service providers’ best interests to take responsibility for their own compliance?
Since the publication of the Final Omnibus Rule in 2013, service providers operating as Business Associates have been directly liable for compliance with certain Privacy Rule and Security Rule requirements. Therefore, even though Business Associates are required to report all security incidents to the Covered Entity they are providing a service to, if it transpires that a data breach was attributable to the Business Associate’s failure to comply with the Privacy Rule and Security Rule requirements, the Business Associate – rather than the Covered Entity – will be considered liable.