Over 10,000 Organizations Targeted in Ongoing MFA-Bypassing Phishing and BEC Campaign
Microsoft has warned of a large-scale phishing campaign targeting Office 365 credentials that bypasses multi-factor authentication (MFA). The campaign is ongoing and more than 10,000 organizations have been targeted by scammers in the past 10 months.
Microsoft reports that one of the phishing runs used emails with HTML file attachments, with the email telling the user about a Microsoft voicemail message that had been received. The HTML file had to be opened to download the message. The HTML file serves as a gatekeeper, ensuring the targeted user was arriving at the URL from a redirect from the original attachment.
The user is redirected to a website that hosts a popular open source phishing kit, which is used to harvest credentials. The user is told that they need to sign in to their Microsoft account to receive the voicemail message and after sign in an email will be sent to the user’s mailbox within an hour with the MP3 voicemail message attached. The user’s email address is auto-filled into the login window and the user only needs to enter their password.
This campaign is referred to as an adversary-in-the-middle (AiTM) phishing attack, as the phishing site sites between the targeted user and the genuine resource they are attempting to log into. Two different Transport Layer Security (TLS) sessions are used, one between the user and the attacker and another between the attacker and the genuine resource.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please Enter Correct Email Address
Your Privacy Respected
HIPAA Journal Privacy Policy
When credentials are entered on the attacker-controlled site, they are passed to the genuine resource. The response from the genuine resource is passed to the attacker, which is then relayed to the user. In addition to harvesting credentials, session cookies are stolen. The session cookie is injected into the browser to skip the authentication process, which still works even if multi-factor authentication is enabled. The phishing kit automates the entire process.
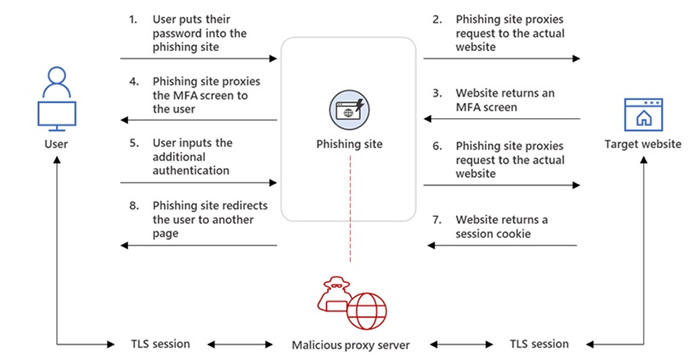
Source: Microsoft
Once the attacker has access to the user’s Office 365 email, the messages in the account are read to identify potential targets for the next phase of the attack. The attacker then sets up mailbox rules that mark certain messages as read and moves them to the archive folder to prevent the user from detecting their mailbox has been compromised. A business email compromise (BEC) scam is then conducted on the targets.
Message threads are hijacked, and the attacker inserts their own content to attempt to get the targeted individual to make a fraudulent wire transfer to an account under the control of the attacker. Since the emails are replies to previous communications, the recipient is likely to believe they are in a genuine conversation with the account owner, when they are only communicating with the attacker.
Microsoft said it takes as little as five minutes from the theft of credentials and session cookies for the first BEC email to be sent. With all replies to the request being automatically sent to the archive, the attacker can simply check the archive for any replies and does so every few hours. They are also able to identify any further potential targets to conduct BEC scams on. While the account compromise is automated, the BEC attacks appear to be conducted manually. Any emails sent or received are manually deleted from the archive folder and sent folder to avoid detection. BEC attacks such as this can involve fraudulent transfers of thousands or even millions of dollars.
Defending against these attacks requires advanced email security solutions that scan inbound and outbound emails and can also block access to malicious websites – an email security solution and a DNS filter for instance. Microsoft also recommends implementing conditional access policies that restrict account access to specific devices or IP addresses. Microsoft also recommends continuously monitoring emails for suspicious or anomalous activities, such as sign-in attempts with suspicious characteristics.
With respect to the MFA bypass, Microsoft stresses that while AiTM attacks can bypass MFA, MFA remains an important security measure and is effective at blocking many threats. Microsoft suggests making MFA implementations “phish-resistant” by using solutions that support Fast ID Online (FIDO) v2.0 and certificate-based authentication.





