The Riskiest Connected Devices in Healthcare
The number of connected devices being used in hospitals continues to grow and while these devices can improve efficiency, safety, and patient outcomes, they have also substantially increased the attack surface, and many of these devices either lack appropriate security features or are not correctly configured.
According to a recent Microsoft-sponsored study by the Ponemon Institute into the current state of IoT/OT cybersecurity, 65% of organizations said their IoT/OT devices were one of the least secured parts of their networks, with 50% reporting an increase in attacks on IoT/OT devices. 88% of respondents said they have IoT devices that are accessible over the Internet, and 51% have OT devices accessible over the Internet. Cybercriminals are increasingly attacking these devices as they are a weak point that can be easily exploited. These devices are the target of malware, ransomware, and are among the main initial access points for malicious actors.
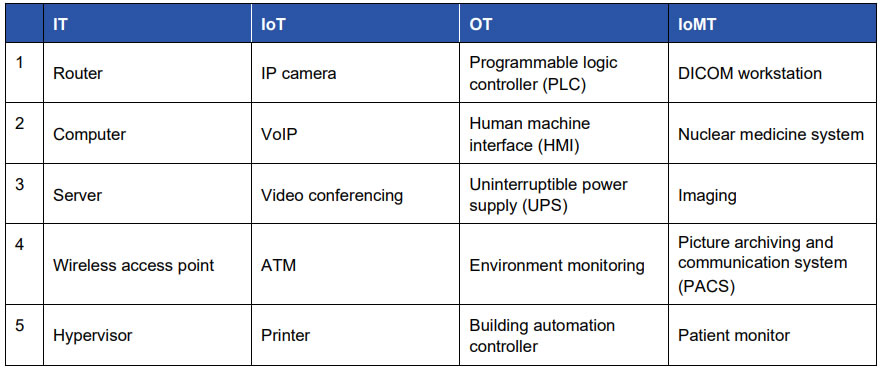
In 2020, Forescout analyzed the types of devices used in enterprise networks to determine which pose the highest risk, and this month has published an updated version of the report. Most of the devices that were rated high risk remain on the updated list, and include networking equipment, VoIP, IP cameras, and programmable logic controllers (PLCs), with hypervisors and human-machine interfaces (HMIs) added this year.
The majority of the riskiest devices are on the list because they are frequently exposed on the Internet or because they are critical to business operations, and vulnerabilities are present in all devices. Almost all organizations rely on a combination of IT, IoT, and OT, with healthcare also relying on IoMT devices. That means almost all organizations face a growing attack surface as they have at least one type of risky device connected to their network.

Get The FREE
HIPAA Compliance Checklist
Immediate Delivery of Checklist Link To Your Email Address
Please Enter Correct Email Address
Your Privacy Respected
HIPAA Journal Privacy Policy
The riskiest devices in each category are detailed in the table below:
Many of the devices included in the list are difficult to patch and manage, which means vulnerabilities are not addressed quickly. IoMT devices are risky because they can provide access to internal networks and can contain valuable patient information, and attacks on these devices can have an impact on healthcare delivery and patient safety. Attacks have been conducted on hospitals that have resulted in fetal monitors being disabled, and in 2020, several attacks were conducted on radiation information systems.
DICOM workstations, nuclear medicine systems, imaging devices, and PACS are all used for medical imaging, and as such can contain highly sensitive patient data. They also commonly run legacy IT operating systems and have extensive network capability for easy sharing of medical imaging data, most commonly using the DICOM standard for sharing files. DICOM was not developed with security in mind, and while DICOM does permit the encryption of data in transit, it is up to individual healthcare organizations to configure encryption. Encryption is not activated in many hospitals, which means medical images are transmitted in clear text and can easily be intercepted and tampered with to include malware. Patient monitors are also amongst the most vulnerable IoMT devices as they commonly communicate using unencrypted protocols, which means communications could be easily intercepted and tampered with. Tampering could prevent alerts from being received.
The key to managing risk is to understand how the attack surface is growing and to conduct a comprehensive risk assessment to understand where the vulnerabilities exist. Those risks can then be subjected to a risk management process and can be reduced to a low and acceptable level. “Once you understand your attack surface, you need to mitigate risk with automated controls that do not rely only on security agents and that apply to the whole enterprise instead of silos like the IT network, the OT network or specific types of IoT devices,” suggests Forescout.